As businesses increasingly adopt cloud-native applications and microservices to drive innovation, they encounter new challenges in managing the complexity of their systems. While these architectures provide scalability and flexibility, they also introduce obstacles in areas like service communication, security, and visibility. That’s where Istio comes in—a robust, open-source service mesh designed to simplify the management of microservices, ensuring seamless communication, enhanced security, and better observability.
This guide will take you through the essentials of Istio, how it works, and why it’s a game-changer for scaling cloud-native applications with confidence.
What is Istio?
Istio is a service mesh that provides a platform for connecting, securing, controlling, and observing microservices. It works as a layer between the application and the network, enabling developers and DevOps teams to manage the complexities of service-to-service communication in modern applications.
For businesses, adopting Istio means enhancing security, improving observability, and optimizing the performance of microservices without significantly increasing the operational burden on developers.
Impact of Istio on microservices
Istio brings a unique approach to managing microservices, mainly through its use of sidecars. These sidecars work alongside each service to handle tasks like routing, security, and data collection, making it easier for businesses to manage complex applications. But in what ways will this impact your current microservices architecture and overall business dynamics? Let us understand by exploring the changes that Istio sidecars bring to the application’s functions for better reliability and performance.
- Increased fault tolerance: Istio sidecars increase your application’s reliability by enabling it to perform the majority of functions even during a service outage. This is because they can be configured to autonomously perform retries a fixed number of times or trigger circuit breakers before redirecting users in case of a service outage or component failure.
- Simplified policy management: Istio provides managers with a centralized control plane, from which they configure security and service settings for multiple components at once. This reduces the hassle of modifying each container and its connected proxies and gives businesses easier authority over their application’s behaviors.
- Reduced dependencies for telemetry: With Istio’s feature to transmit telemetry data, you get access to readily available insights into the performance of your application. This also significantly reduces the need for dedicated services to monitor application performance which saves you more time for analysis. Furthermore, it can be readily integrated with other observability platforms such as Grafana to analyze telemetry data with greater accuracy.
How Does Istio Service Mesh Work?
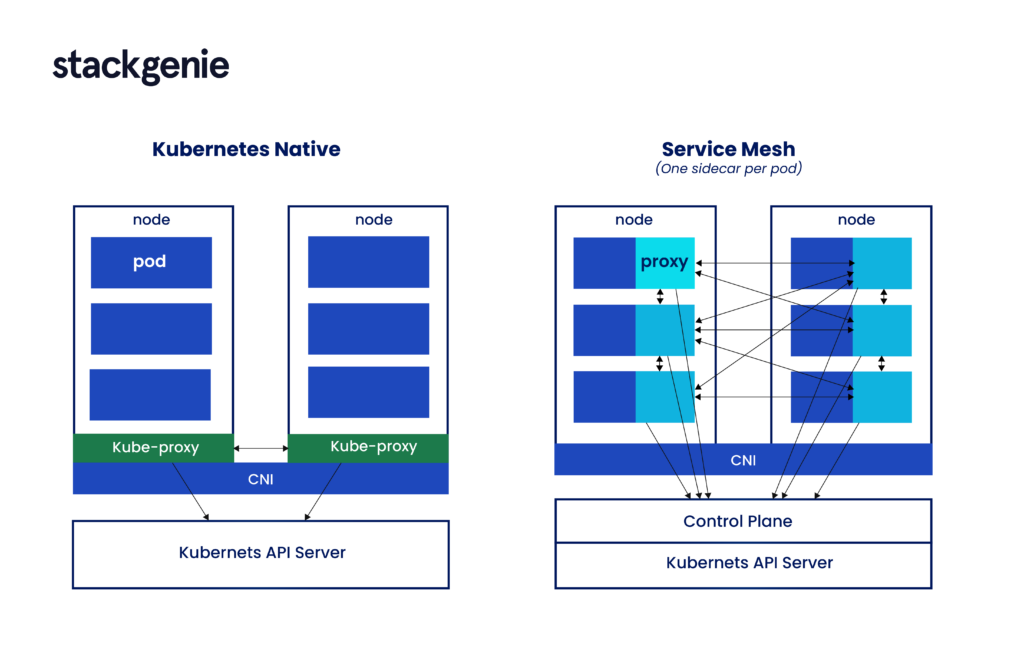
Much like other service meshes, Istio works by using sidecars which are proxies attached to each microservice instance. Once configured, these sidecars intercept any new request and redirect it to the appropriate service using preset rules. The sidecars can also transmit telemetry data to deliver in-depth insights into application performance and error rates.
The functions and configurations of these sidecars are achieved broadly through two planes which are the control plane and the data plane. Both of these planes are connected to all microservice instances within your architecture. Let us understand what these planes are for and how they can be used.
Istio Data Plane / Envoy:
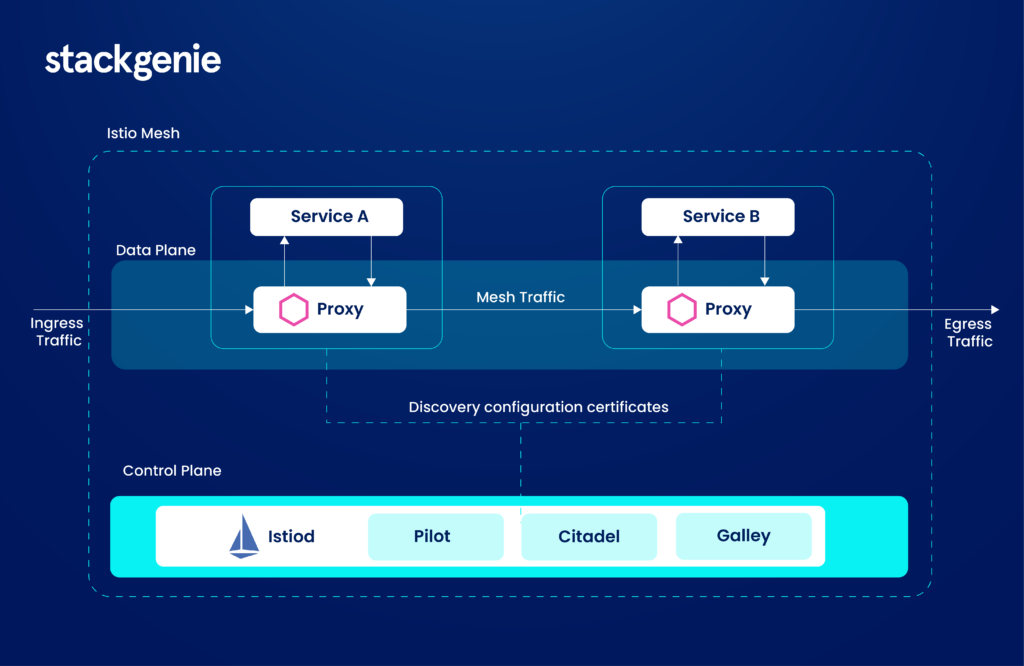
The data plane is the component responsible for handling the actual traffic between microservices. It consists of lightweight Envoy proxies that are deployed as sidecars along with each service instance. When a service receives a request, the Envoy proxy processes it first before it reaches the actual service directly.
The proxy can apply various preprogrammed configurations, such as load balancing, retries, timeouts, and circuit breaking, to ensure reliable communication between services. Additionally, the data plane enforces security protocols like mutual TLS (mTLS) and granular identity-based access to encrypt traffic and authenticate services helping secure data in transit and preventing unauthorized access.
The Envoy proxies also gather telemetry data, including metrics and logs, which provide insights into service performance and health. Envoy captures this data as it processes traffic, forwarding it to Istio’s control plane or other observability tools for analysis.
Istio Control Plane / Istiod:
The control plane in Istio enables the administrator to adjust the configuration, management, and orchestration of the data plane. Naturally, this also gives control over the Envoy proxies deployed with all microservice instances. It provides a centralized interface for defining the policies, rules, and configurations that govern how traffic flows through the microservices architecture.
One of the primary components of the Istio control plane is Istiod (formerly known as Pilot), which handles the distribution of configuration information to the data plane. Istiod provides the necessary service discovery, traffic management, and configuration updates. When changes such as deploying a new version of a service, Istiod distributes these changes to the relevant proxies, ensuring that they are consistently applied across the environment.
Furthermore, the control plane integrates with external systems and tools, allowing for seamless observability and monitoring with a set of APIs that developers and operators can use to interact with Istio. This makes it easier to automate tasks, integrate with CI/CD pipelines, and manage configurations on demand.
Top 5 Benefits of Using Istio Service Mesh
Using Istio, in particular, holds many benefits that businesses can enjoy, ranging from increased developer productivity to reduced architecture complexity. To understand these benefits better in terms of their tangible impact, we have listed the top reasons why development teams choose Istio to improve their existing solutions.
1. Improved Security:
Istio significantly enhances security within microservices architectures through mechanisms such as mutual Transport Layer Security (mTLS). This mechanism encrypts traffic between services and ensures that the client and server authenticate each other before establishing a connection to prevent unauthorized access.
Istio also provides fine-grained access control through authorization policies. Administrators of the application can readily define rules that specify which services can communicate with each other. Role-based access control (RBAC) is also possible, and it updates access for all users based on their roles and authority.
2. Additional Deployment Options:
A general concern when using sidecar proxies is the challenge of excessive resource consumption. Since these sidecars are attached to every single component, it takes additional computing power to process user requests. This is why Istio introduced an extra deployment option known as ‘Ambient Mode’.
Ambient mode creates general traffic routing rules and access controls that apply to all microservices rather than doing it with individual sidecars. Administrators also have an easier time adjusting configurations as it simplifies application architecture further and reduces resource consumption.
3. Enhanced Observability
Istio enables the collection of various types of telemetry data, including metrics, logs, and distributed traces. Accessing these metrics will give you insights into performance indicators like latency, request rates, and error rates, allowing teams to track the health and performance of individual services after deployment.
The collected logs also offer detailed information about interactions within services, while distributed tracing provides a visual representation of request paths across microservices. This allows teams to identify bottlenecks, latency issues, and failures in complex service interactions, which leads to faster troubleshooting and issue resolution.
4. Traffic Management & Testing:
The load-balancing capabilities of Istio allow you to customize redirecting rules based on various factors. These factors include the user’s geographic location, network latency, and service history. Companies can also perform canary deployments using Istio by setting instructions to distribute portions of traffic to new application versions.
The ability to rapidly modify traffic distribution in this manner is excellent for testing new features without modifying the production experiences for all users. If users experience functional issues in the new application version, Istio can automatically rollback the traffic to previous stable instances.
5. Network Resilience:
Istio’s features protect your application from cascading failures usually arising due to component dependencies. The main feature that makes this possible is circuit breaking, which enables Istio to detect if any service instance is facing issues. Once detected, Istio can reroute all traffic from the faulty service to other instances.
All of these features to improve network resilience can always be counted on despite any updates to Istio since they only issue stable binary releases. This means that all versions of Istio have been thoroughly tested in multiple scenarios before launch. Teams have immense confidence in integrating new versions of Istio without worrying about major compatibility issues.
6. Vast Integration Capabilities:
One of the key strengths of Istio is its ability to work seamlessly with a wide range of existing tools and technologies. Such integration can be used with various observability tools, such as Prometheus for metrics collection, Grafana for visualization, and Jaeger or Zipkin for distributed tracing. This interoperability enables teams to gain deep insights into their application performance and behavior, without overhauling their existing observability stack.
Additionally, Istio integrates well with popular cloud-native technologies and platforms, such as Kubernetes, making it a natural choice for organizations that have adopted microservices and container orchestration. Its compatibility with cloud providers and services enhances its usability across diverse environments, whether with on-premises, cloud, or hybrid setups.
How Istio Work with Kubernetes?
If your application already uses microservices with Kubernetes to orchestrate containers, then you might wonder how Istio would integrate and refine policy management and security. While Kubernetes does have rudimentary load-balancing features, Istio adds an additional layer of control over each individual container, which leads to the following enhancements:
- Cross-container security: Rather than having a general access policy over all containers, Istio introduces the option to set security measures for each individual container. It also adds features such as mTLS for Kubernetes to facilitate data encryption.
- Individual service performance analytics: To gain deeper insights into performance, Istio’s sidecars are used as they can collect logs and latency figures for each component. This helps you solve the analytical limitations of Kubernetes.
- Centralized control over proxies: The control plane from Istio drastically improves the experiences of customizing proxy behaviors by giving teams a centralized point for control. This improves the uniformity of policies across all service instances.
Best of all, the installation of Istio into Kubernetes is very simple since Istio can automatically inject the Envoy proxy as a sidecar into the Kubernetes pods of your microservices. This process allows Istio to manage traffic between services transparently, without requiring code changes to the applications.
Transform Service Management and Application Security With the Istio Service Mesh
As we can see, implementing Istio for your project is great for gaining more control over your application’s internal policies and interactions. Every single feature, from traffic distribution to circuit breaking, collectively protects your services from functional errors and external threats.
However, configuring Istio and integrating it with your existing microservices architecture may seem like a daunting endeavor that requires a lot of planning and expertise. In such scenarios, it is helpful to have the help of Stackgenie – A reputed Istio consulting services provider.
Our Istio consulting services for microservices are ideal if you want a turnkey solution to integrate Istio within your applications. Our Kubernetes-certified team is ready to help you manage any complexities that arise from introducing new frameworks like Istio. Contact us now to learn more about how we can help you get started with augmenting your application with a popular service mesh like Istio.
FAQs
1. Do I really need Istio for my microservices application?
If your microservices application needs a reliable framework for managing multiple components, incorporating Istio will be required to form a solid foundation. This will eventually help you manage the increased architectural complexity while delivering reliable service management capabilities that support your operational goals.
2. What are the key considerations to know before implementing Istio?
Before implementing Istio, it’s essential to consider the complexity it introduces to your microservices architecture. Organizations should evaluate their team’s familiarity with service meshes and the learning curve associated with Istio’s various components, such as the control plane and sidecar proxies. Additionally, it’s crucial to assess the existing infrastructure, as Istio may need changes to deployment practices.
3. What language is Istio written in?
Istio is primarily written in Go (Golang). This language was chosen for its efficiency, ease of concurrency, and performance, making it well-suited for building scalable network services and microservices architectures. Some components may also involve other languages, such as JavaScript for certain web-based interfaces, but Istio’s core functionality relies on Go.
4. Is Istio more suitable for small projects or large enterprises?
Istio is generally more suitable for large enterprises rather than small projects. Its feature set is designed to manage complex microservices architectures, involving numerous services that require advanced traffic management, security, and observability. For larger enterprises, successfully implementing and managing Istio often requires specialized knowledge. This is why organizations find it beneficial to seek enterprise-grade Istio support to navigate the intricacies of its deployment and configuration.
5. Is Stackgenie one of the pro service providers?
Yes, Stackgenie is recognized as a professional service provider specializing in Istio consulting services. Our certified team helps manage traffic, security, and observability for optimized performance and streamlined service management.


