Istio provides features that enable you to manage a network for deployed services with secure communication, monitoring, version based load balancing or traffic splitting and much more. Istio works with modern cloud native applications because it requires little to no service code changes with automatic sidecar proxy injection that intercepts all network traffic between services.
There are several ways to install Istio including a Helm chart, Kubernetes manifests, and finally using an Istio Operator.
In this blog, we are going to focus solely on how to deploy Istio using the Istio Operator in Azure AKS.
Benefits Of Service Mesh
Before going to the deployment phase, let’s talk about the key benefits to service mesh:
- Increase release flexibility. Teams can exercise greater control over both their testing procedures and deployments.
- Ensure high availability and fault tolerance. Teams can deploy a service mesh to enable setup retries and failover and to test code paths through fault injections.
- Maintain secure communications. Teams can authenticate, authorise and encrypt service-to-service communications. For example, service meshes are useful to manage service encryption via mutual Transport Layer Security (mTLS) and ensure secure connections.
- Gain greater visibility. Service mesh deployments ensure observability and monitoring in the form of latency metrics, distributed tracing support and real-time service-to-service monitoring
What Do We Do?
In order to deploy the Istio on to the Kubernetes cluster, we use the Istio operator(still in beta) .Istio operator manages all aspects of the Istio service mesh installations. Instead of manually maintaining the Istio mesh installation and Istio CLI versions, you can use the Istio operator.
The operators and the operator pattern are a way to automate repeatable tasks. In Kubernetes, an operator uses custom resources and a controller to manage applications and their components.
Using the Istio CLI and the istioctl operator init command, we can deploy the Istio operator controller to the Kubernetes cluster.
Prerequisites
Let’s see what are the requirements for configuring the Istio operator.
- You need to have a running Azure AKS Cluster, AKS Cluster Deployment.
- We use a latest version (available at the time) of Istio that is 1.13.
- Also, we use Sockshop, a demo online shop website which is a microservice architecture, cloud native application.
Name | Version |
Istio | 1.13 |
Kubernetes | 1.22 |
Sockshop | – |
Installation & Configurations
Following are the steps involved in for the installations and configuration of istio and the demo sockshop microservice application into a kubernetes cluster.
The Installation Configuration Profiles provide customization of the Istio control plane and of the sidecars for the Istio data plane. Please see the following installation profiles,
- default: enables components according to the default settings of the IstioOperator API. This profile is recommended for production deployments and for primary clusters in a multicluster mesh.
- demo: configuration designed to showcase Istio functionality with modest resource requirements.
- minimal: same as the default profile, but only the control plane components are installed. This allows you to configure the control plane and data plane components (e.g., gateways) using separate profiles.
- external: used for configuring a remote cluster that is managed by an external control plane or by a control plane in a primary cluster of a multicluster mesh.
- empty: deploys nothing. This can be useful as a base profile for custom configuration.
- preview: the preview profile contains features that are experimental. This is intended to explore new features coming to Istio. Stability, security, and performance are not guaranteed.
Istio Installation Steps:
- Download the istioctl binary from the git repository. Depending on your operating system, for this we use linux_amd64.
$ wget https://github.com/istio/istio/releases/download/1.13.4/istioctl-1.13.4-linux-amd64.tar.gz - Extract the binary and add it to your PATH environment.
- $ sudo tar -C /usr/local/bin/ -xzvf istioctl-1.13.4-linux-amd64.tar.gzNext, run a pre-check command to see if our cluster has any issues. (optional).
$ istioctl x precheck
✔ No issues found when checking the cluster. Istio is safe to install or upgrade!
- To get started, check out https://istio.io/latest/docs/setup/getting-started/Now, we can deploy the Istio operator using istioctl command.
$ istioctl operator init
Installing operator controller in namespace: istio-operator using image: docker.io/istio/operator:1.13.4
Operator controller will watch namespaces: istio-system
✔ Istio operator installed
- ✔ Installation completeWith the operator installed, now create a mesh by deploying an IstioOperator resource.
$ kubectl apply -f – <<EOF
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
namespace: istio-system
name: istiocontrolplane
spec:
profile: default
EOF
- Note: The Istio control plane (istiod) will be installed in the istio-system namespace by default. Also, the profiles provide customization of the Istio control plane and of the sidecars for the Istio data plane. In this we use the default profile.Finally, to make sure istio installation is successful, we can list all the components under the istio-system, and istio-operator namespace.
$ kubectl get iop -A
NAMESPACE NAME REVISION STATUS AGE
istio-system istiocontrolplane HEALTHY 2m50s
$ kubectl get all -nistio-operator
NAME READY STATUS RESTARTS AGE
pod/istio-operator-76989c777f-j42jd 1/1 Running 0 5m45s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/istio-operator ClusterIP 10.0.75.42 8383/TCP 5m44s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/istio-operator 1/1 1 1 5m45s
NAME DESIRED CURRENT READY AGE
replicaset.apps/istio-operator-76989c777f 1 1 1 5m45s
$ kubectl get all -nistio-system
NAME READY STATUS RESTARTS AGE
pod/istio-ingressgateway-76dcc86449-mj9tg 1/1 Running 0 25s
pod/istiod-845cbb7785-bgwfs 1/1 Running 0 36s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/istio-ingressgateway LoadBalancer 10.0.16.12 20.109.16.103 15021:32062/TCP,80:30992/TCP,443:30667/TCP 25s
service/istiod ClusterIP 10.0.57.101 15010/TCP,15012/TCP,443/TCP,15014/TCP 36s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/istio-ingressgateway 1/1 1 1 26s
deployment.apps/istiod 1/1 1 1 37s
NAME DESIRED CURRENT READY AGE
replicaset.apps/istio-ingressgateway-76dcc86449 1 1 1 26s
replicaset.apps/istiod-845cbb7785 1 1 1 37s
NAME REFERENCE TARGETS MINPODS MAXPODS REPLICAS AGE
horizontalpodautoscaler.autoscaling/istio-ingressgateway Deployment/istio-ingressgateway /80% 1 5 1 26s
horizontalpodautoscaler.autoscaling/istiod Deployment/istiod /80% 1 5 1 37s
- Optional – Now, we can install some additional features to the istio system to get more observability. Telemetry Addons.
$ kubectl apply -f https://raw.githubusercontent.com/istio/istio/1.13.4/samples/addons/grafana.yaml
$ kubectl apply -f https://raw.githubusercontent.com/istio/istio/1.13.4/samples/addons/jaeger.yaml
$ kubectl apply -f https://raw.githubusercontent.com/istio/istio/1.13.4/samples/addons/kiali.yaml
$ kubectl apply -f https://raw.githubusercontent.com/istio/istio/1.13.4/samples/addons/prometheus.yaml
Sockshop Installation Steps:
Once the Istio installation is completed, we can deploy our application into our cluster with istio injection label. Following are the steps involved in for the installations and configuration of istio and the demo sockshop microservice application into an Kubernetes cluster.
- Sockshop installation can be done in a single manifest apply.
- $ kubectl apply -f https://stackgenie.local/manifests/istio-sockshop/sockshop-istio-complete-demo.yamlNow that the Sockshop services are up and running, we need an Istio Gateway and VirtualService to access the app from the internet.
- $ kubectl apply -f https://stackgenie.local/manifests/istio-sockshop/sockshop-istio-gateway.yamlGet INGRESS_HOST to connect to istio gateway.
$ export INGRESS_HOST=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}’)
$ echo $INGRESS_HOST
- That’s it, finally you can access your application from the outside world using the load balancer DNS record, this will vary depending on your infrastructure setup.
$ curl -I $INGRESS_HOST
HTTP/1.1 200 OK
x-powered-by: Express
accept-ranges: bytes
cache-control: public, max-age=0
last-modified: Tue, 21 Mar 2017 11:31:47 GMT
etag: W/”21f0-15af0a320b8″
content-type: text/html; charset=UTF-8
content-length: 8688
date: Thu, 11 Jan 2021 16:27:55 GMT
x-envoy-upstream-service-time: 3
server: istio-envoy
Note: If Kubernetes is deployed in a non-cloud environment then INGRESS_HOST is IP of any Kubernetes worker node, since service istio-ingress gateway is of type NodePort in that case.
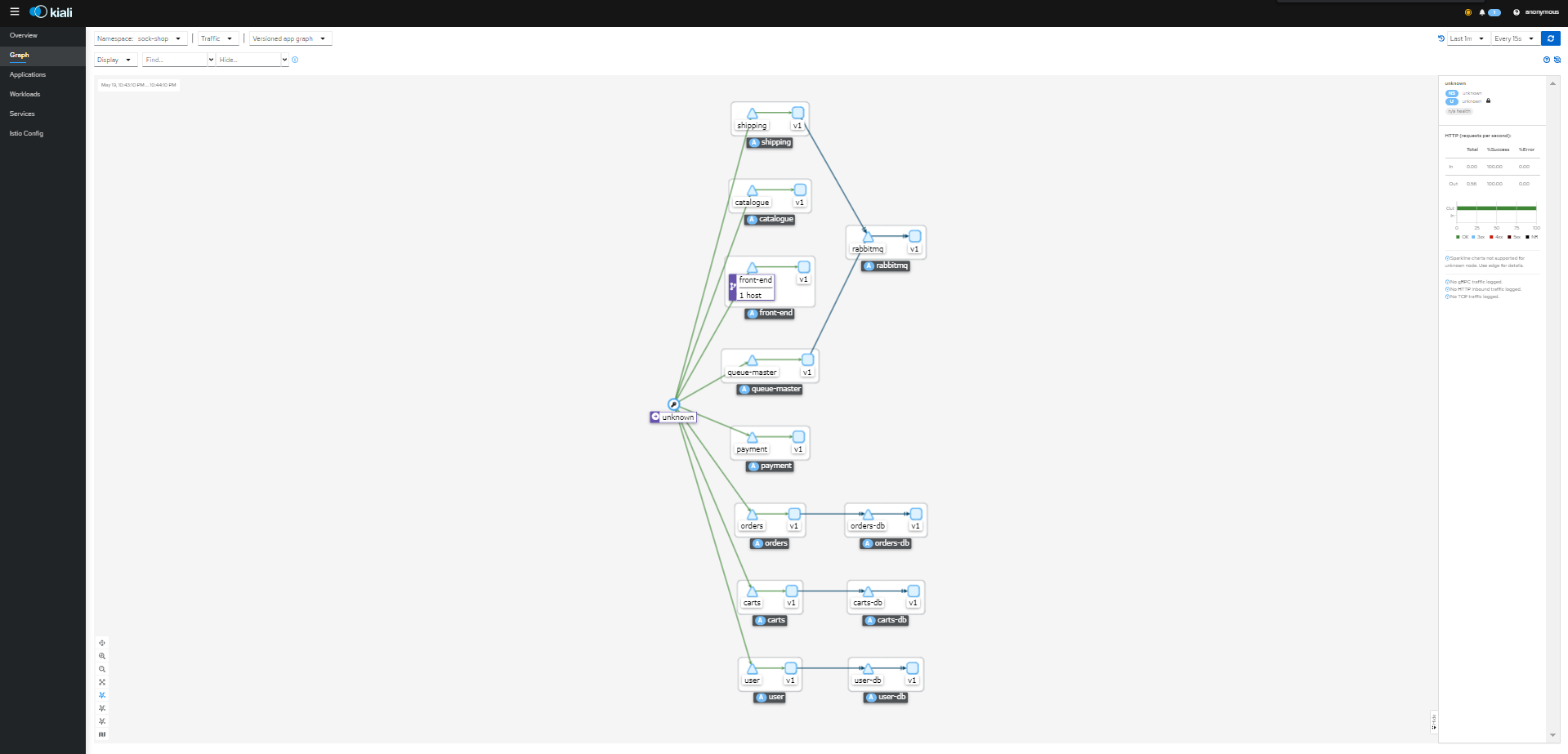
Istio Observability Console – Kiali
Kiali is an observability console for Istio with service mesh configuration capabilities. It helps you to understand the structure of your service mesh by inferring the topology, and also provides the health of your mesh. Kiali provides detailed metrics, and a basic Grafana integration is available for advanced queries. Distributed tracing is provided by integrating Jaeger.
To access Kiali console please follow these steps,
- Port-forward kiali service to localhost to access the dashboard.
- $ kubectl port-forward -nistio-system svc/kiali 20001Now, access kiali dashboard from your localhost on port 20001 http://localhost:20001
 Note: This is only available, if Step: 7 from “Istio Installation Steps” is executed.
Note: This is only available, if Step: 7 from “Istio Installation Steps” is executed.
Conclusion
This short technical document is on how Istio and the addons come together. A clearer picture of the behaviour of the microservices, also understand the interactions with other microservices, and are easily able to identify behaviours in the system. Istio Service Mesh has offered tremendously great new capabilities that are changing the way companies deal with their security and observability. While we continue to harness Istio’s capabilities targeted towards improving the resilience of infrastructure, we hope this blog helped you to get an understanding of the key features that the Istio service mesh offers for managing, securing, and observing microservices.
Looking for help with your Kubernetes or want help with your Kubernetes implementation strategy? Reach out to us and see how we can help.


